Zeroing in On Port 0 Traffic in the Wild
On this website we present additional information about our PAM 2021 paper Zeroing in on Port 0 Traffic in the Wild and provide access to our Port 0 Active Measurement Service.Port 0 Active Measurement Service
We provide a Port 0 Active Measurement Service where we publish IPv6/IPv4 addresses responsive on port 0, and traceroute results to the whole IPv6 address space and one IP address in each publicly routable prefix in IPv4 to interested researchers. The Port 0 Active Measurement Service consists of an openly accessible one and a registration-first service.To get free access to this registration-first service, you can send a quick registration email. We use the gathered data for statistical purposes and might very occasionally send a survey or other requests for feedback.
Referencing the Port 0 Service
If you are using data from the Port 0 Active Measurement Service in your publication, please refer to it with the following reference:
@inproceedings{maghsoudlou2021zeroing,
title = {Zeroing in on Port 0 Traffic in the Wild},
author = {Maghsoudlou, Aniss and Gasser, Oliver and Feldmann, Anja},
booktitle = {Proceedings of the 2021 Passive and Active Measurement Conference},
year = {2021},
location = {Cottbus, Germany},
numpages = {17},
doi = {10.1007/978-3-030-72582-2_32},
publisher = {Springer},
address = {Berlin, Germany},
}
The same reference applies to the open and registered service. [bib]
Paper
Abstract. Internet services leverage transport protocol port numbers to specify the source and destination application layer protocols. While using port 0 is not allowed in most transport protocols, we see a non-negligible share of traffic using port 0 in the Internet.In this study, we dissect port 0 traffic to infer its possible origins and causes using five complementing flow-level and packet-level datasets. We observe 73 GB of port 0 traffic in one week of IXP traffic, most of which we identify as an artifact of packet fragmentation. In our packet-level datasets, most traffic is originated from a small number of hosts and while most of the packets have no payload, a major fraction of packets containing payload belong to the BitTorrent protocol. Moreover, we find unique traffic patterns commonly seen in scanning. In addition to analyzing passive traces, we also conduct an active measurement campaign to study how different networks react to port 0 traffic. We find an unexpectedly high response rate for TCP port 0 probes in IPv4, with very low response rates with other protocol types. Finally, we will be running continuous port 0 measurements and providing the results to the measurement community.
Paper. Read the final version of our paper at arXiv.org: arXiv:2103.13055
Authors. Aniss Maghsoudlou, Oliver Gasser, Anja Feldmann
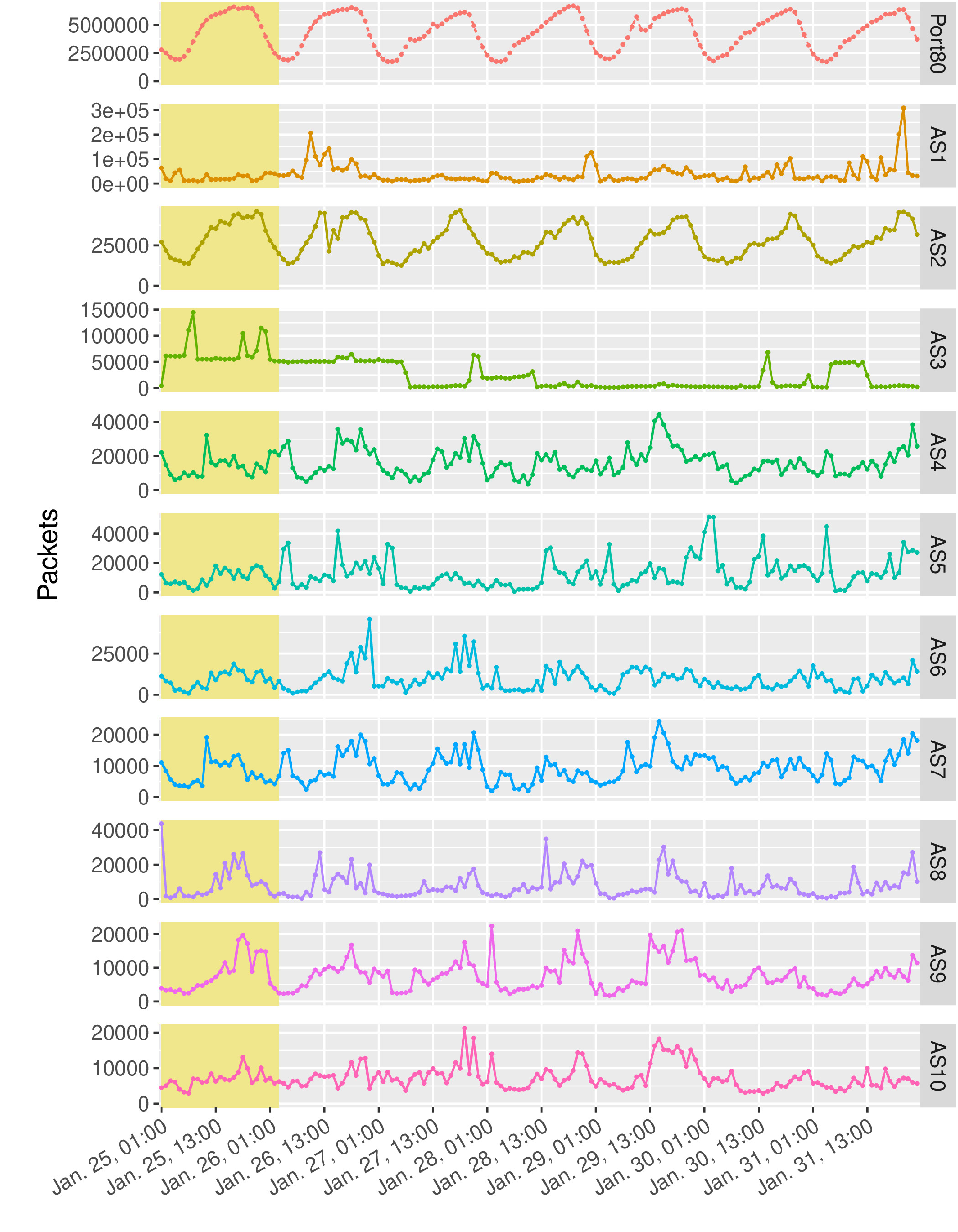
Additional Plots
We provide the following additional plot for in-depth analysis accompanying the evaluations in our paper.
Reproducibility
We publish data and scripts to reproduce our analysis at Edmond, Open Research Data Repository of the Max Planck Society, to guarantee long-term availability.Dataset DOI: 10.17617/3.5f
Contact
Aniss Maghsoudlou aniss [AT] mpi-inf.mpg.deOliver Gasser oliver.gasser [AT] mpi-inf.mpg.de